Overview
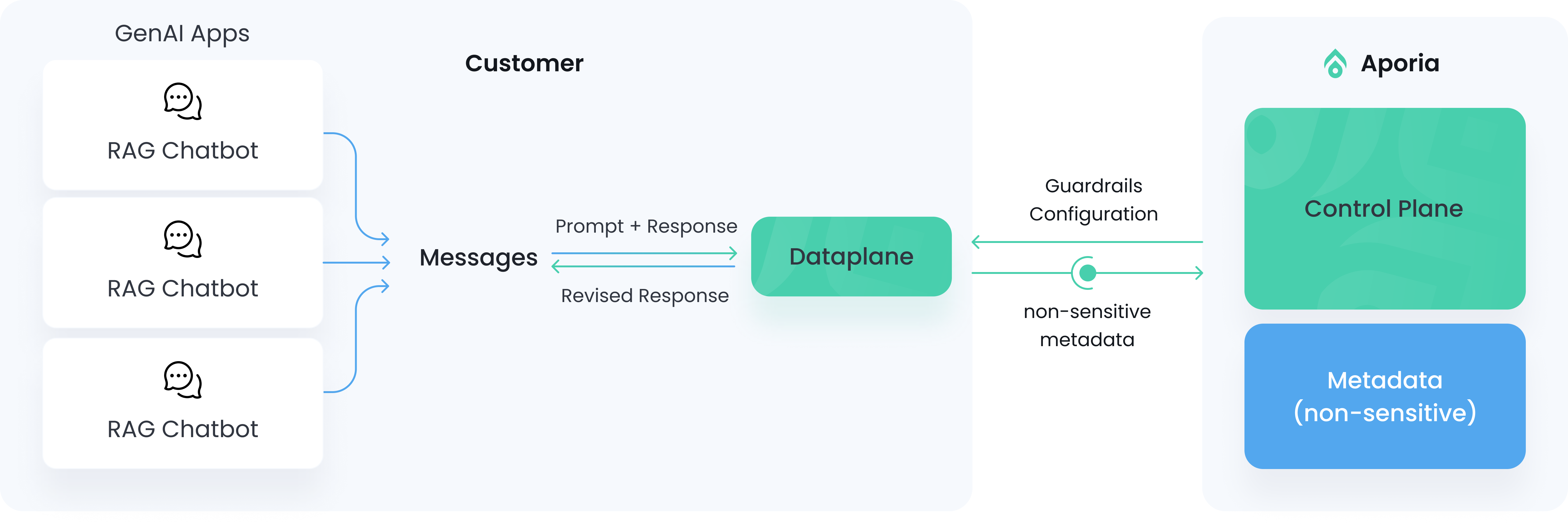
The Aporia architecture is split into two planes to avoid sensitive data exposure and simplify maintenance.- The control plane lives in Aporia’s cloud and serves the policy configuration, along with the UI and metadata.
- The data plane can be deployed in your cloud environment, runs the policies themselves and provides an OpenAI-compatible endpoint.
Architecture
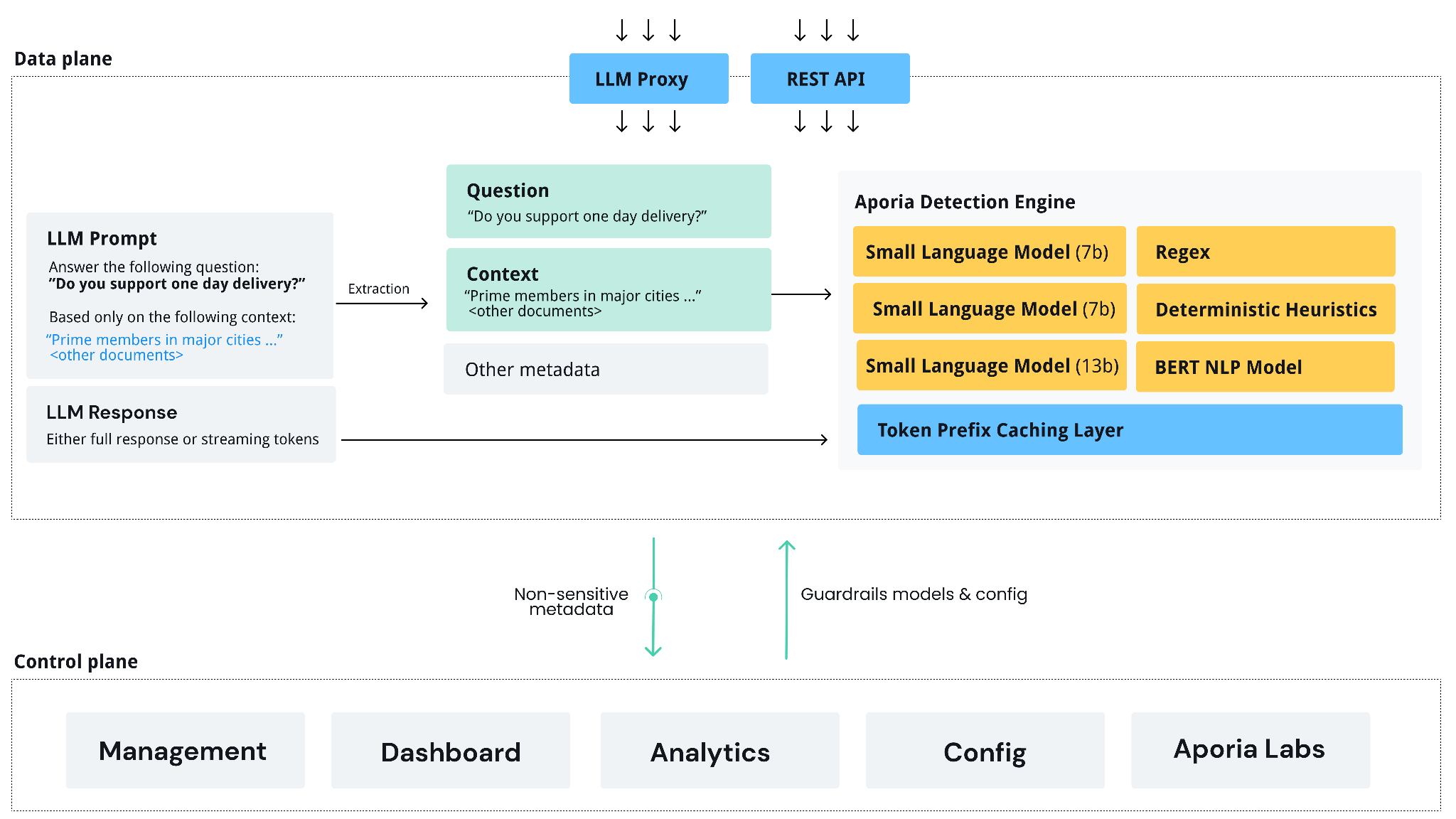
Built on a robust Kubernetes architecture, the data plane is designed to expand horizontally, adapting to the volume and demands of your LLM applications. The data plane lives in your cloud provider account, and it’s a fully stateless application where all configuration is retrieved from the control plane. Any LLM prompt & response is processed in-memory only, unless users opt to storing them in an Postgres database in the customer’s cloud. Users can either use the OpenAI proxy or call the detection API directly. The data plane generates non-sensitive metadata that is pushed to the control plane (e.g. toxicity score, hallucination score).Data plane modes
The data plane supports 2 modes:- Azure OpenAI mode - In this basic mode, all policies run using Azure OpenAI. While in this mode you can run the data plane without any GPUs, this mode does not support policy fine-tuning, and the accuracy/latency of the policies will be lower.
- Full mode - In this mode, we’ll run our fine-tuned small language models (SLMs) on your infrastructure. This achieves our state-of-the-art accuracy + latency but requires access to GPUs.
Dependencies
- Kubernetes (e.g. Amazon EKS)
- Postgres (e.g. Amazon RDS)
- RabbitMQ (e.g. Amazon MQ)